この記事は最終更新日より 1 年以上経過しています。
画像やリンクが無効になっている可能性もあるのでご了承下さい。
画像やリンクが無効になっている可能性もあるのでご了承下さい。
www ドメインは https サポートさせてるから新しい証明書作ろう。
ベリサインとか認証局通す金ないから自前の認証局でオレオレ証明書なるけど
これ作るかなと。
ここんとこ鯖ネタばっかですまそ (汗
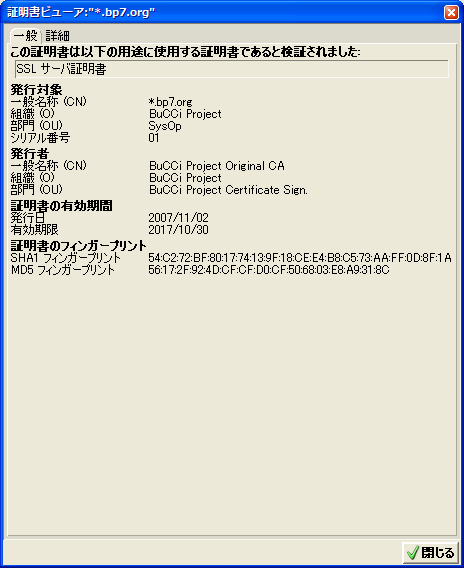
14:56 一応完成した証明書をブラウザから検証した SS も添付。
再作成何度もやったら割と楽に作れるようになったけど、忘れっぽいので
ログ残し。見てもあまりわからないかもしれない (笑
# openssl genrsa -des3 -out server.key 1024
Generating RSA private key, 1024 bit long modulus
......++++++
........................................................................++++++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
# openssl rsa -in server.key -out server_nopass.key
Enter pass phrase for server.key:
writing RSA key
# openssl req -new -days 3650 -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [JP]:
State or Province Name (full name) [Kanagawa-ken]:
Locality Name (eg, city) [Yokohama-city]:
Organization Name (eg, company) [BuCCi Project]:
Organizational Unit Name (eg, section) [Administrator]:SysOp
Common Name (eg, your name or your server's hostname) []:*.bp7.org
Email Address [admin@example.org]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# ls
server.csr server.key server_nopass.key
# openssl ca -in server.csr -keyfile /path/to/cakey.pem -cert /path/to/cacert.pem -out server.crt
Using configuration from /usr/share/ssl/openssl.cnf
Enter pass phrase for /path/to/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Nov 2 03:43:07 2007 GMT
Not After : Oct 30 03:43:07 2017 GMT
Subject:
countryName = JP
stateOrProvinceName = Kanagawa-ken
organizationName = BuCCi Project
organizationalUnitName = SysOp
commonName = *.bp7.org
emailAddress = admin@example.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Cert Type:
SSL Server
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
AE:A7:95:73:66:68:AE:A6:42:C2:CE:AC:04:65:37:7A:CA:4A:E0:07
X509v3 Authority Key Identifier:
keyid:DA:42:91:DF:C6:28:63:CF:CD:CB:AD:E4:61:44:BA:1F:3A:29:2E:82
DirName:/C=JP/ST=Kanagawa-ken/L=Yokohama-city/O=BuCCi Project/OU=SysOp/CN=*.bp7.org/emailAddress=admin@example.org
serial:00
Certificate is to be certified until Oct 30 03:43:07 2017 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
# vi ssl.conf
SSLCertificateFile /path/to/server.crt
SSLCertificateKeyFile /path/to/server_nopass.key
#


コメント